 |
| ghulamahmedbinsaeed.blogspot.com |
Backlinks are very important for every Blog or Websites. You can get quality Backlinks by commenting on high PR sites, Joining forms and community sites, joining question and answer websites, guest posting, submitting article to social bookmarking and social networking websites. There are so many other ways also available on the internet to get Quality Backlinks.
Why it is required to get quality Backlinks from High PR website?
Getting quality Backlinks from the high PR websites help blogs to improve page rank easily. That’s why every blogger want to link the blog or website to high PR websites.
When you create a link, it can be a Dofollow or Nofollow link. There are two questions frequently asked by bloggers.
What is a Dofollow or Nofollow link?
How to check whether the link is Dofollow or Nofollow?
How to Get Top 5 Quality Backlinks in 15 Minutes?
There are so many high PR-9 websites available to get quality Backlinks but here I have listed 5 websites from where you can get quality Backlinks in just 15 minutes.
1) Google+ PR-9
As you know that Google+ is one of the best and leading social media network who is on the top of the list with PR-9 after Google PageRank Update on 06th Dec 2013.
Google is known for his Name & Fame, so it provides Nofollow as well as Dofollow links.
How to get Dofollow link from Google+ towards the blog?
Step-1:
Log in to your Google+ Account (Create a new account if you don’t have)
Step-2:
Go to your profile page > Click on About Section
Step-3:
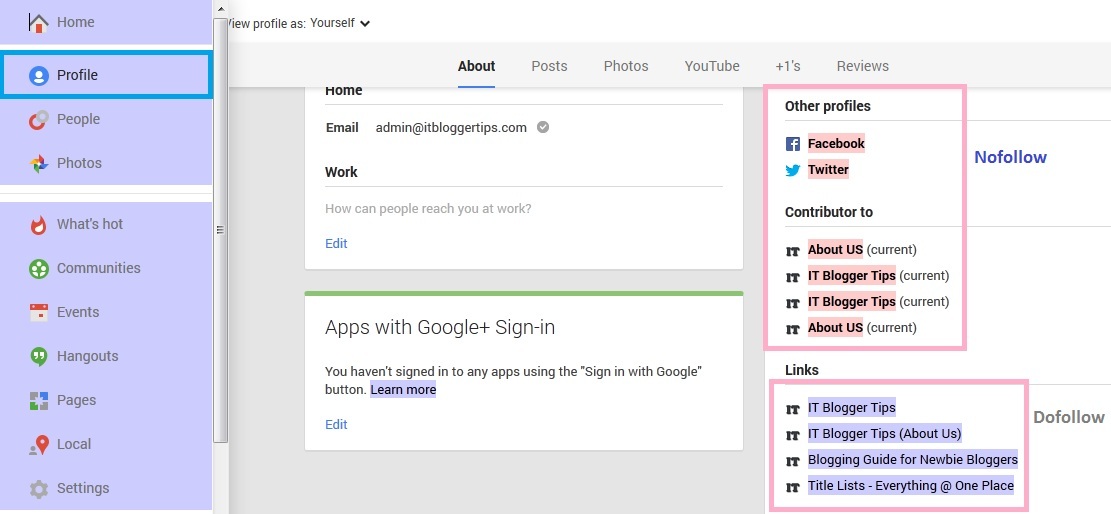
Now scroll down to Links and click on Edit option.
Add your links here and these links will be Dofollow links. You can see in below snapshot, the links which are highlighted in light pink color are Nofollow and the links which are highlighted in light grey color are Dofollow.
You can also check our Google+ About Page here.
 |
| ghulamahmedbinsaeed.blogspot.com |
2) YouTube PR-9
YouTube is the best website who gives you PR-9 NoFollow as well as DoFollow Backlinks.
You can easily add your blog or website link in the Description or in the About section, but these are considered as NoFollow Backlinks.
When you add your website or blog URL to the “Associated Website” tab then you get DoFollow backlink on YouTube.
How to get DoFollow Backlink on YouTube?
First verify your account using the link (youtube.com/verify) and submit your website to Google Webmasters. (If you have not submitted to your website to Google Webmasters, Click Here)
After verification, Login to your YouTube Account using Gmail credentials.
Go to Channel Setting > Click on View Additional Features (youtube.com/features)
Now add your website on “Associated Website” under Advanced section.
The message should appear as SUCCESS.
 |
| ghulamahmedbinsaeed.blogspot.com |
3) Adobe PR-9
Adobe.com is the best PR-9 website that gives you NoFollow Backlinks to your website or blog.
How to get No-follow Backlinks from Adobe.com?
First sign up with Adobe.com website.
An email will be sent to your email address to confirm the subscription. Just confirm your subscription and create an awesome profile.
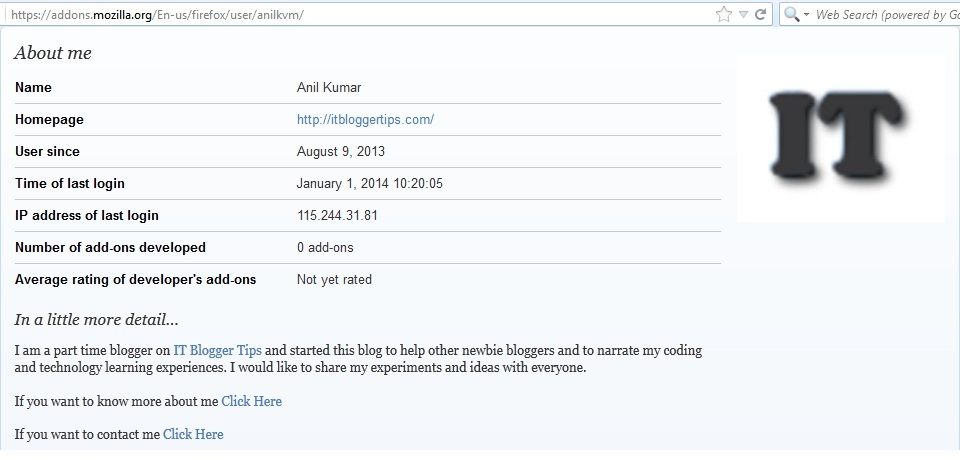
Note: There is no option to put your website link at your profile page.
Visit to Adobe Forum and write here original problem with your blog’s URL.
This is the only way to get Backlink from Adobe.
4) Mozilla.org PR-9
Everybody knows that Mozilla is the highly reputed website with PageRank 9.
How to get Dofollow quality Backlinks from Mozilla?
First register to addons.mozilla.org/En-us/firefox/users/register
Fill the complete details along with your website homepage and click on Register button.
An email will be sent to your e-mail address to confirm the subscription.
Confirm your activation and login to check out your profile page.
 |
| ghulamahmedbinsaeed.blogspot.com |
5) Opera.com PR-9
Open Opera website and click on Sign Up button and fill the registration form.
An email will be sent to your e-mail address to confirm the subscription. Once you confirmed the subscription, you can create your profile page just like Mozilla.
Opera gives you NoFollow Backlink.
Bonus: Quality Backlink from PR-8 Website
6) Yahoo Answers! PR-8
This is best choice to get quality Backlinks on your website as well as on your posts too.
Join Yahoo Answers and become regular visitor to give answer of questions and put the link of your website as a reference to get quality Backlink and huge visitor too.
Yahoo Answers! gives you only NoFollow link but it is good for Domain Authority.
If you liked this article then spare 5 secs to share with your friends and colleagues.





















